IoT security is one of the most pressing problems of our time
Over the next two years device numbers (more precisely, inputs and outputs for IoT devices) are expected to rise from 9 to 500 units per household. This smart environment will revolve around the user. With so many devices, traditional security methods will become obsolete, because the user simply won’t be able to monitor them all.
What’s more, Industrial Revolution 4.0 envisages the creation of almost fully automated, smart module-driven industries involving almost no people. This is the so-called industrial internet of things (IIoT). Due to the complexity of such an environment, human intervention is generally reserved for troubleshooting only; however, undetected cybercriminal activity can still lead to disastrous consequences.
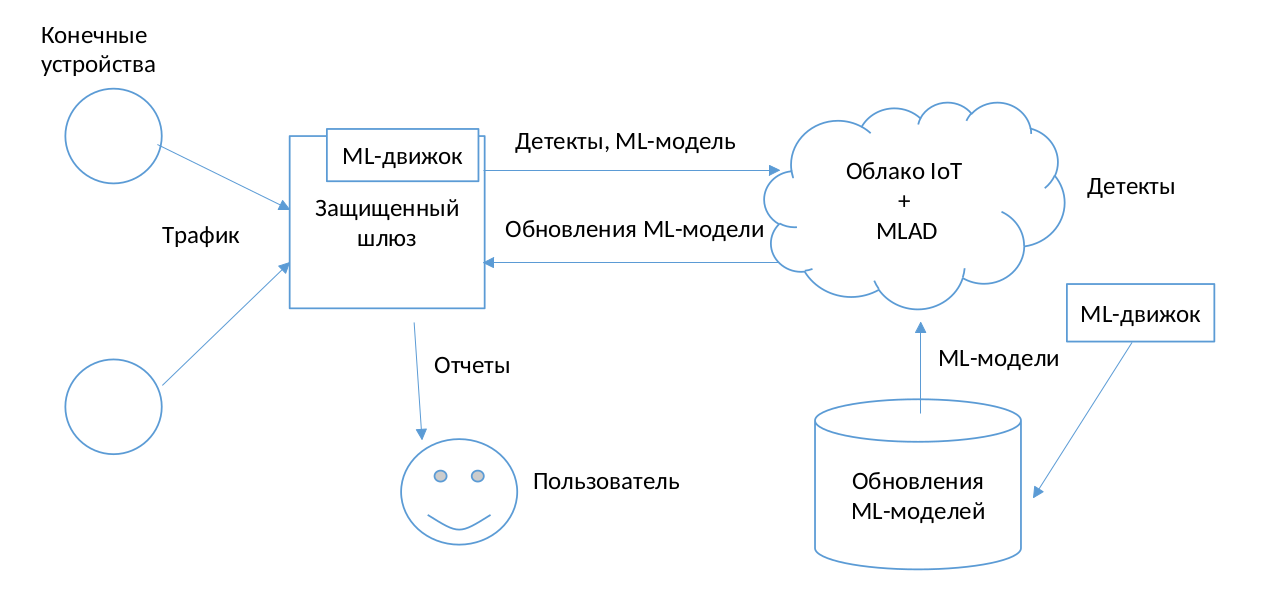
In both technological environments – IoT and IIoT – it is important to identify abnormal device behavior at the earliest possible stage, regardless of the cause: cybercriminal activity or a technological malfunction. It is preferable for data received from a device to be processed as close as possible to its location, since this approach (so-called edge computing) improves response times and reduces the amount of traffic transmitted to the cloud.
Machine learning lies at the core of edge computing
Two important aspects of edge computing are the miniaturization and energy performance of the hardware platform. We believe that machine-learning methods, in particular spiking neural networks (SNN), are the most promising tool for energy-efficient processing of multiple information flows in an IoT or IIoT environment.
Our approach is founded on the premise that each IoT or IIoT device has its own behavioral profile – a repertoire of incoming commands, actions, and context-dependent reactions that characterizes it
By using modern machine-learning techniques, it is possible to create a profile of the typical behavior of a device.
We are developing a methodology to create such profiles in order to detect anomalies in the behavior of devices at the following levels of network traffic:
- At the level of raw network traffic (we analyze network packets and identify packets that are atypical for the device)
- At the MQTT traffic level
- At the telemetry level of I(I)oT devices As part of this approach, we use technologies similar to those deployed in Kaspersky MLAD.
We are also exploring ways to provide users with information about anomalies using 3D models of the environment.